Table of Contents
How to Enable QUIC on LiteSpeed Web Server
In most cases, it is easy to enable QUIC. Simply open UDP port 443, and QUIC is on by default.
QUIC (or, Quick UDP Internet Connections) is an experimental protocol initially developed by Google in 2012, and announced publicly the following year. QUIC is a good choice for those looking to reduce connection-establishment time and improve congestion control. Since version 5.2, LiteSpeed provides the first production-grade mass-market QUIC implementation available for the public. If you want to serve your web content using the QUIC protocol, LiteSpeed is the solution.
There is no configuration change required in LSWS. For control panel users, QUIC is turned on by default for Apache HTTPS vhosts. All that is required is to open UDP port 443.
Required:
- HTTPS with trusted certificate
- UDP port 443 open at the firewall
How to Open UDP Port 443 at the Firewall
QUIC runs a stream-multiplexing protocol over Transport Layer Security (TLS) on top of UDP instead of TCP. Be sure you've enabled the port with both TCP and UDP. Most of the time, TCP 443 is enabled.
You can quickly check to make sure it is listening by running
netstat -lupn | grep 443
udp 0 0 127.0.0.1:443 0.0.0.0:* 18918/litespeed (ls udp 0 0 x.x.x.x:443 0.0.0.0:* 18918/litespeed (ls udp 0 0 :::443 :::* 18918/litespeed (ls
QUIC itself should auto listen on UDP port 443, but any firewall that is running must be configured so that port 443 is open.
You will need to identify which firewall is running, such as firewalld, iptables, csf, or other external firewalls.
cPanel
If there is no extra firewall such as CSF, UDP 443 should be enabled by default. If CSF is used, you need to enable it at the CSF level.
ConfigServer Security & Firewall → csf - ConfigServer Firewall → Firewall Configuration → IPv4 Port Settings → UDP_IN and UDP_OUT should enable 443.
Also make sure that UDPFLOOD is set to Off 0.
Plesk
Firewalld
Enable it with the following command:
firewall-cmd --zone=public --add-port=443/udp --permanent firewall-cmd --reload
iptables
Enable it with the following command:
iptables -I INPUT -p udp --dport 443 -j ACCEPT /sbin/service iptables save /sbin/service iptables restart
How to Test UDP Incoming and Outgoing Connections
Although you have enabled UDP on 443 on your server, it may be blocked by the data center at the route/switch/firewall level. To verify this, you can run the following:
Verify with NC command
Test Incoming
To test incoming UDP connections to your server, you can run the following command from somewhere else, such as your local VM, or your other test client machine, but not within your server to be tested:
[root@OLS-PS-EL /]# nc -v -u your_server_ip 443 Ncat: Version 6.40 ( http://nmap.org/ncat ) Ncat: Connected to your_server_ip:443
Test Outgoing
To test outgoing UDP connections on your server, you can run the following within your testing server:
nc -v -u www.google.com 443 Ncat: Version 6.40 ( http://nmap.org/ncat ) Ncat: Connected to 74.125.24.104:443.
Verify with TCPDUMP
Sometimes that nc -vu command is not enough to verify UDP 443 port unless it will return some information back
You can verify it with tcpdump, e.g.
Run tcpdump on the website's server.
tcpdump -vv udp port 443 -X
Run nc command from any client server.
nc -vu YOUR_DOMAIN 443
and you should see some output on server if there's any UDP port 443 traffic in and out.
How to Verify QUIC is Enabled
- Check header:
alt-svc:quic=":443"; v="35,37", or "http/2+quic/37"
- Check quic connections:
chrome://net-internals/#quic
- There’s a Chrome extension which will allow you to see the protocols being used on any website. Install HTTP/2 and SPDY indicator, and you will see a lightning bolt in the Chrome toolbar. Blue indicates HTTP/2 is enabled. Green indicates HTTP/2 + QUIC. Hover over the lightning bolt to see a more detailed list of protocols in action. Tip: You should see the QUIC indicator on dynamic pages with a regular refresh. If not, press
CTRL + SHIFT + Rto request a fresh copy of the page.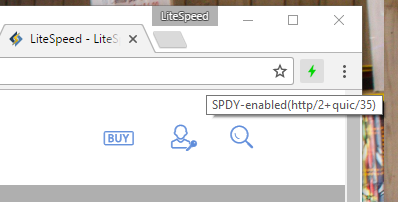
Checklist
If QUIC is not working for you, keep these requirements in mind:
- Must have QUIC enabled in GUI/conf
- Must use either Chrome or Opera with QUIC enabled
- Must not use self-signed certificates only trusted certificates will work
- Must setup SSL Settings correclty
- Must have UDP Port 443 open at firewall
- QUIC will not work with a proxy front end like CloudFlare
- QUIC will only apply to https, not http
- QUIC can be enabled at the server level, listener level or virtual host level
- QUIC won't work with LSWS 5.2.8 anymore as Chrome only speaks “quic/43”, while LSWS 5.2.8 only supports up to “quic/39”
Looking to disable QUIC, or enable it at only the Virtual Host, or Listener Level? See How to Disable QUIC on LiteSpeed Web Server.
Troubleshooting
CloudFlare doesn't support QUIC yet
Please keep in mind that CloudFlare doesn't support QUIC yet at the time of this writing. If you are behind CloudFlare, please disable it before testing/using QUIC.
Possibly Google Chrome has not enabled QUIC by default
At some point we noticed that Google Chrome decided to temporarily disable QUIC by default. Some users explicitly have to enable QUIC under chrome://flags. This may not be the case for you, but it's a good idea to check whether QUIC is enabled in Chrome.
Possibly bad cached SSL certificates
Sometimes, especially when the site in question has encountered an SSL/TLS error before, Chrome will save the certificate in cache and cause QUIC to be unable to establish a connection. In this case, it can simply be fixed by clearing the browser cache.
UDP rate limiting option in CSF should be disabled
If CSF used, UDP rate limiting option is normally disabled by default. You should see UDPFLOOD = “0”. However, if you have enabled it somehow, please disable it before running any QUIC checker, such as http3check.net .
# Outgoing UDP Flood Protection. This option limits outbound UDP packet floods. # These typically originate from exploit scripts uploaded through vulnerable # web scripts. Care should be taken on servers that use services that utilise # high levels of UDP outbound traffic, such as SNMP, so you may need to alter # the UDPFLOOD_LIMIT and UDPFLOOD_BURST options to suit your environment # # We recommend enabling User ID Tracking (UID_INTERVAL) with this feature UDPFLOOD = "0" UDPFLOOD_LIMIT = "100/s" UDPFLOOD_BURST = "500" # This is a list of usernames that should not be rate limited, such as "named" # to prevent bind traffic from being limited. # # Note: root (UID:0) is always allowed UDPFLOOD_ALLOWUSER = "named"
LF_SPI needs to be turned off when CSF used
LF_SPI in CSF should be turned off (set LF_SPI = 0).
According to CFS, LF_SPI option configures csf iptables as a Stateful Packet Inspection (SPI) firewall – the default (which means LF_SPI = 1 by default). If the server has a broken stateful connection tracking kernel then this setting can be set to 0 to configure csf iptables to be a Static firewall, though some funtionality and security will be inevitably lost.


